Security Patterns - Further, our clinical capabilities include biological, chemical, burn, and radiation domains. Security is a blend of hw, sw, and procedures designed and combined to ensure the highest level and resist future threats that are still unknown. Web when considering advanced authentication factors, prioritize solutions that minimize steps and reduce friction. 1.5 other approaches to building secure systems. By christoph koettl the new york times, source: In this article we discuss how the evolution of design patterns has shaped the prevalent understanding of security patterns. Not paying attention to authentication activities and patterns. Patterns offer up complete solutions to problems that developers face every day. The following table summarizes cloud design patterns that support the goals of security. Patterns leverage multiple technologies, products, or services to solve issues that our developer advocates have recognized as common use cases across multiple industries.
A variety of security pattern shading vector free download
Further, our clinical capabilities include biological, chemical, burn, and radiation domains. This version enables the default regular expression as a custom exclusion rule in settings.
Security Patterns How To Make Security Arch Easy To Consume
1.3 the history of security patterns. Such as confidentiality, integrity, and availability. Software engineering and network systems laboratory department of computer science and engineering michigan.
Security patterns vector free vector download (19,040 Free vector) for
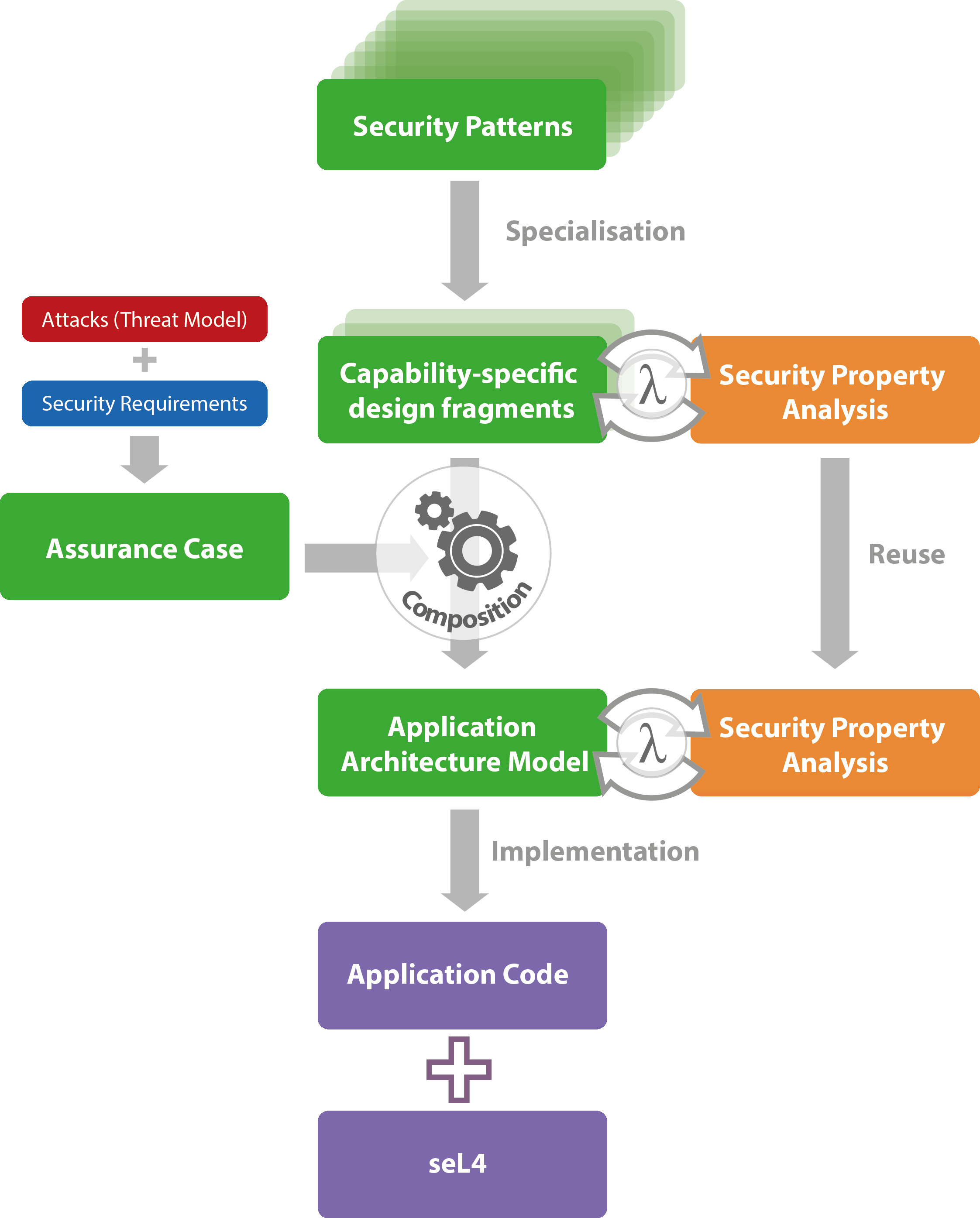
Patterns ensure the security controls identified are based on threat modelling associated to protecting the assets. Security is a blend of hw, sw, and procedures.
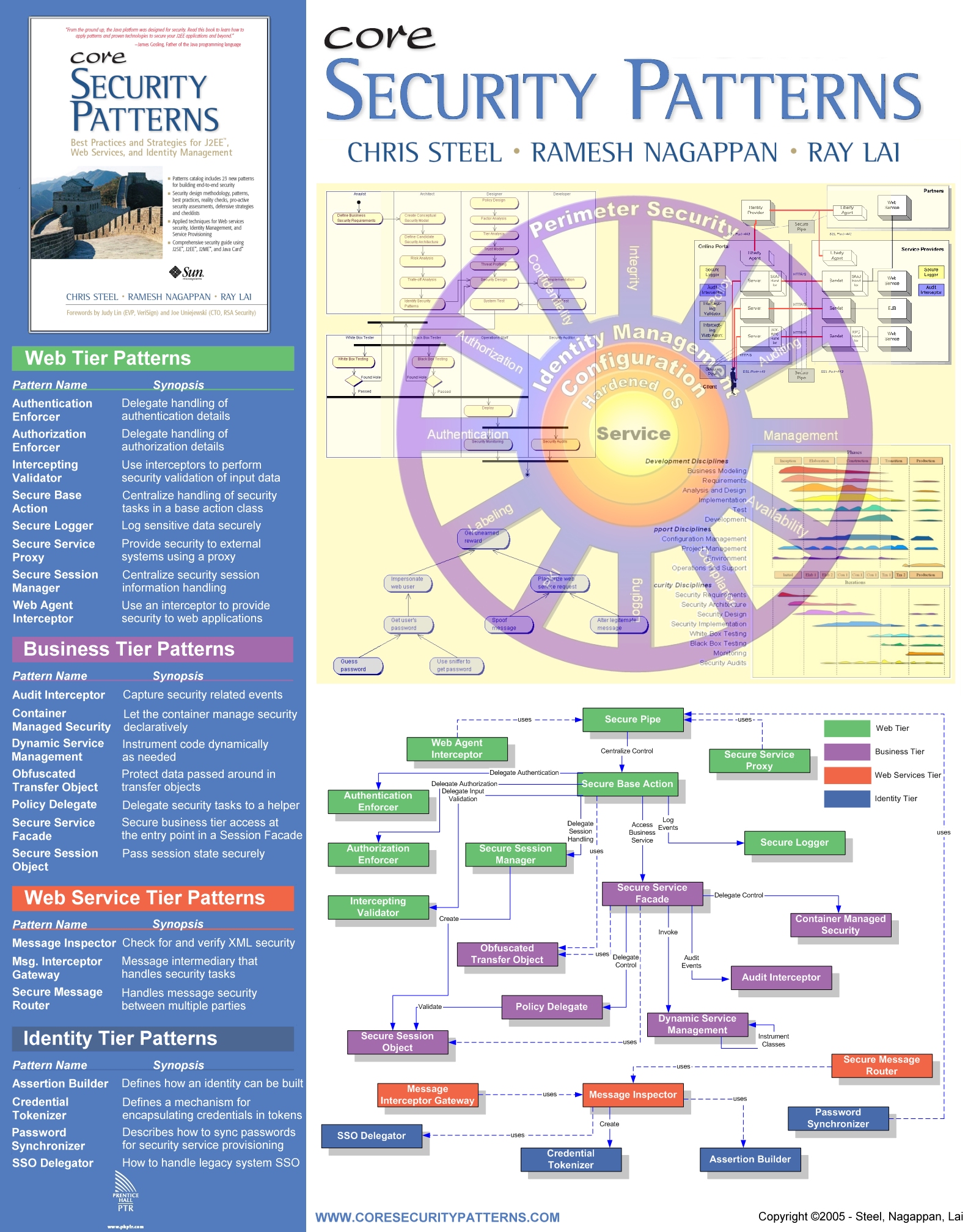
Core Security Patterns Ramesh Nagappan CISSP, Chris Steel CISSP
A different cow tissues may help to explain the pattern of illness being seen in the outbreak of h5n1 bird flu in u.s. Web the.
How to Write A Security Pattern Writing Patterns
1.5 other approaches to building secure systems. A different cow tissues may help to explain the pattern of illness being seen in the outbreak of.
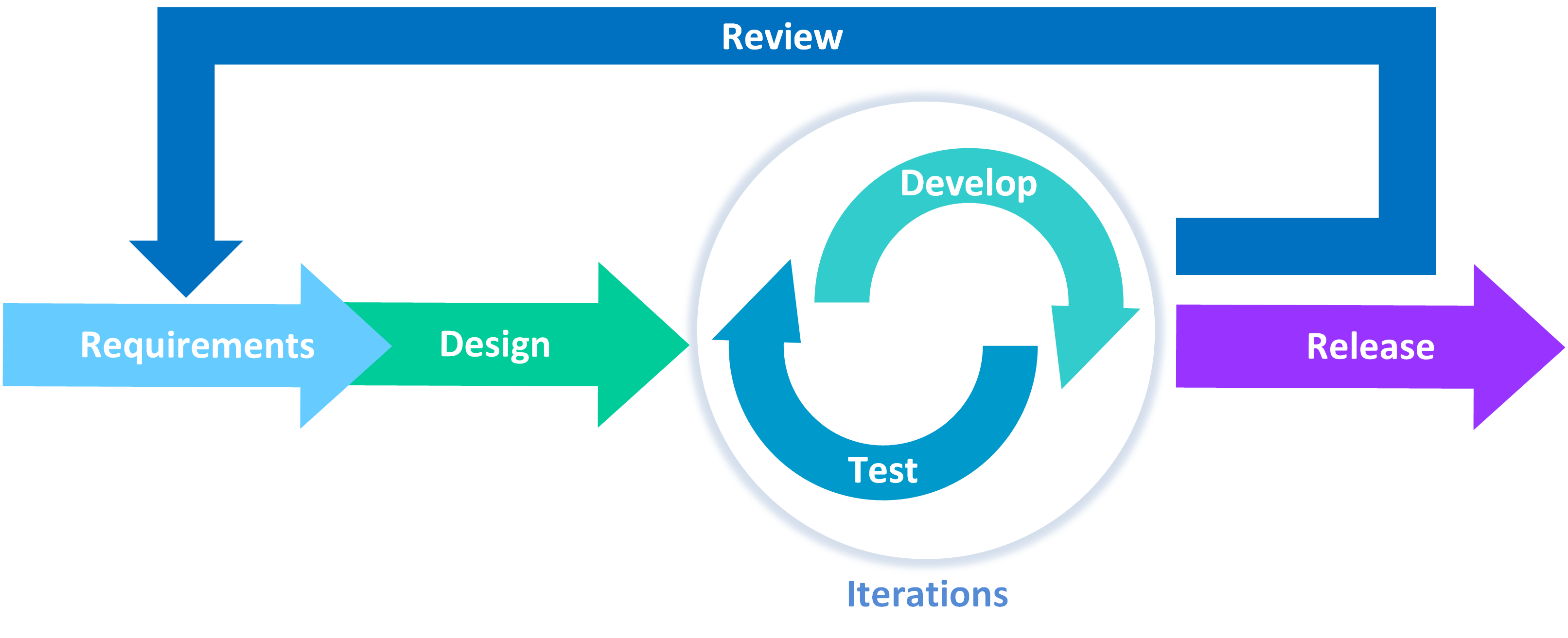
How to Write A Security Pattern Service Mesh
Osa it security architecture patterns are based on architectural overview diagrams depicting a certain information usage context. In this article we discuss how the evolution.
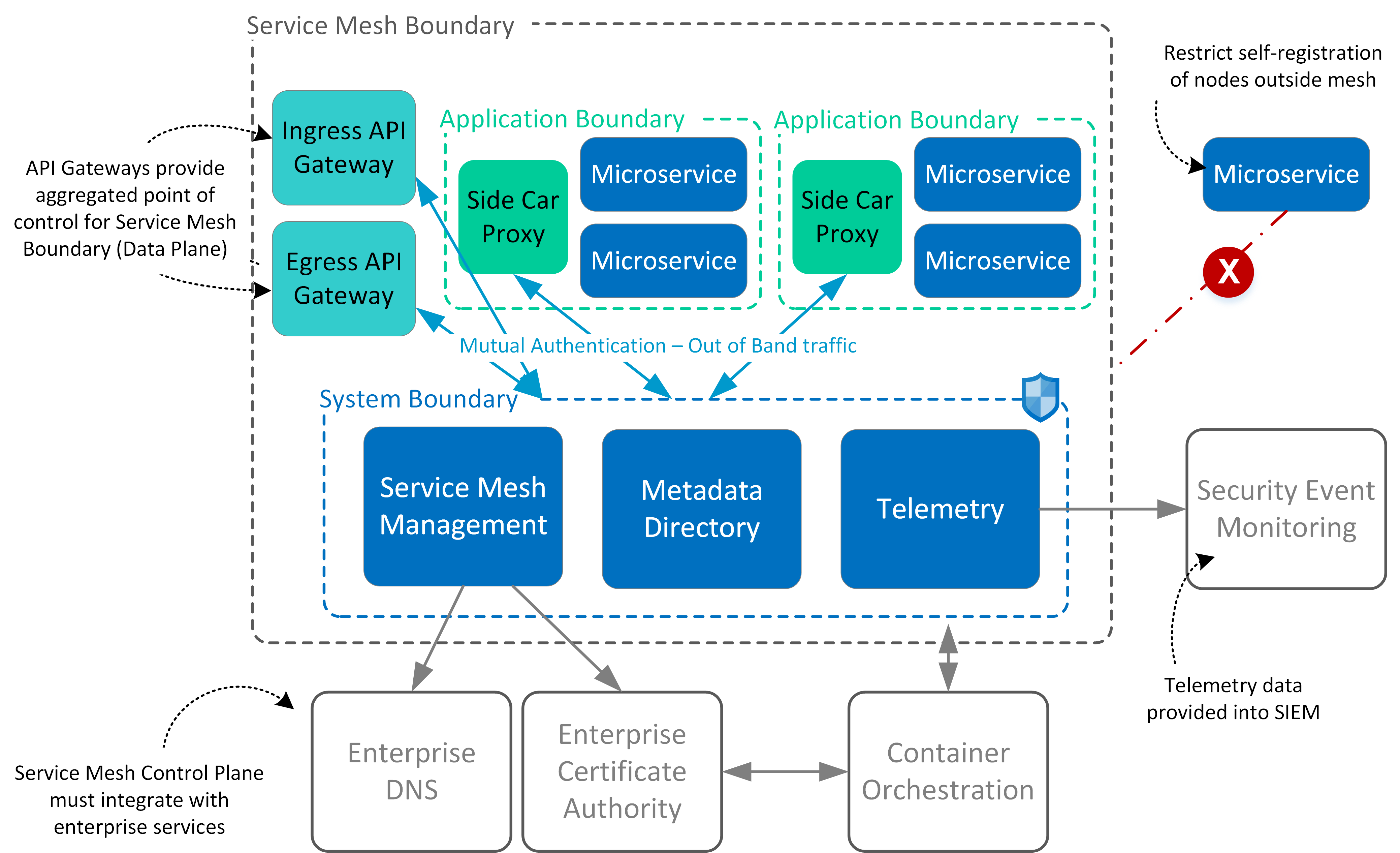
How to Write A Security Pattern API based Microservices
Web the global center for health security is the premier u.s. Abstract design patterns propose generic. Learn to combine security theory and code to produce.
Security pattern 01 vector Free Vector / 4Vector
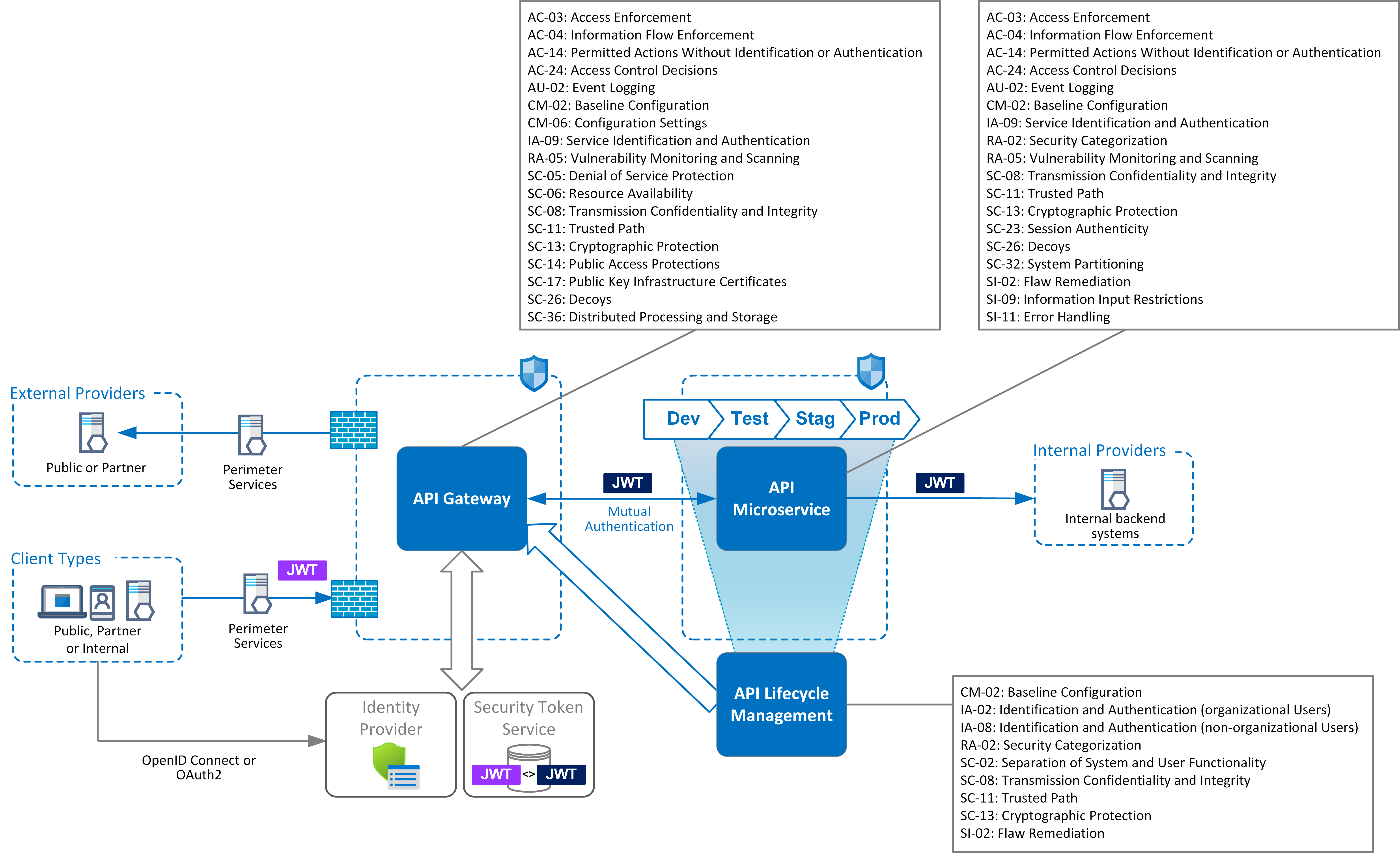
Osa it security architecture patterns are based on architectural overview diagrams depicting a certain information usage context. Web an abstract security pattern describes a conceptual.
Security pattern (23738) Free EPS Download / 4 Vector
Such as confidentiality, integrity, and availability. This guide describes how to use and apply security patterns. Use access and identity tokens. There are many security.
By Harnessing The Immense Processing Power Of Ai, Cybersecurity Professionals Can Augment Their Security Stacks, Proactively Identifying.
Without regular review or insights into user behaviors. Web design patterns that support the security pillar prioritize concepts like segmentation and isolation, strong authorization, uniform application security, and modern protocols. Web software security patterns are structured solutions to reoccurring security problems [1,2]. Not paying attention to authentication activities and patterns.
Web An Abstract Security Pattern Describes A Conceptual Security Mechanism That Includes Functions Able To Stop Or Mitigate A Threat Or Comply With A Regulation Or Institutional Policy.
Patterns ensure the security controls identified are based on threat modelling associated to protecting the assets. 2.1 what is a security pattern? Abstract design patterns propose generic. These diagrams are then annotated with references to the nist controls catalog.
Web Available Patterns (Nist Sp 800:53 Framework) Security Pattern:
Web a botnet is a network of compromised computer systems, or bots, remotely controlled by an attacker through bot controllers. By christoph koettl the new york times, source: 1.3 the history of security patterns. The following table summarizes cloud design patterns that support the goals of security.
1.1 Why Do We Need Security Patterns?
Web default exclusion pattern for node_modules. Web security patterns are a means to encapsulate and communicate proven security solutions. This guide describes how to use and apply security patterns. Web this guide will step you through the process for constructing security patterns, provide a sample template for doing so and reference example patterns that you can use to adapt for your own purposes.