Security Pattern - In the proceeding sections of this guide, i’ll provide reference how the security pattern for source code management.it’s probably not the best example for demonstrating the value of security patterns but does simplify the example so that we can focus on the process to. Web the government accused russia’s domestic intelligence agency, the federal security service, or f.s.b., of a pattern of “malign activity” in britain and europe, including hacking and leaking. Maintains standards for threat and control taxonomies to. Highlights the reasons for choosing the pattern and provides. Web security patterns would benefit greatly from a standardized and comprehensive pattern catalog. In context of a security problem and how it affects the asset. Web security patterns for microservice architectures. Web a security pattern is typically defined by the following following 4 characteristics. He has been a contract professor at politecnico di milano, teaching cryptography to the master course of computer science from 2004 to 2010. A role) that is passed to the guard of resource.
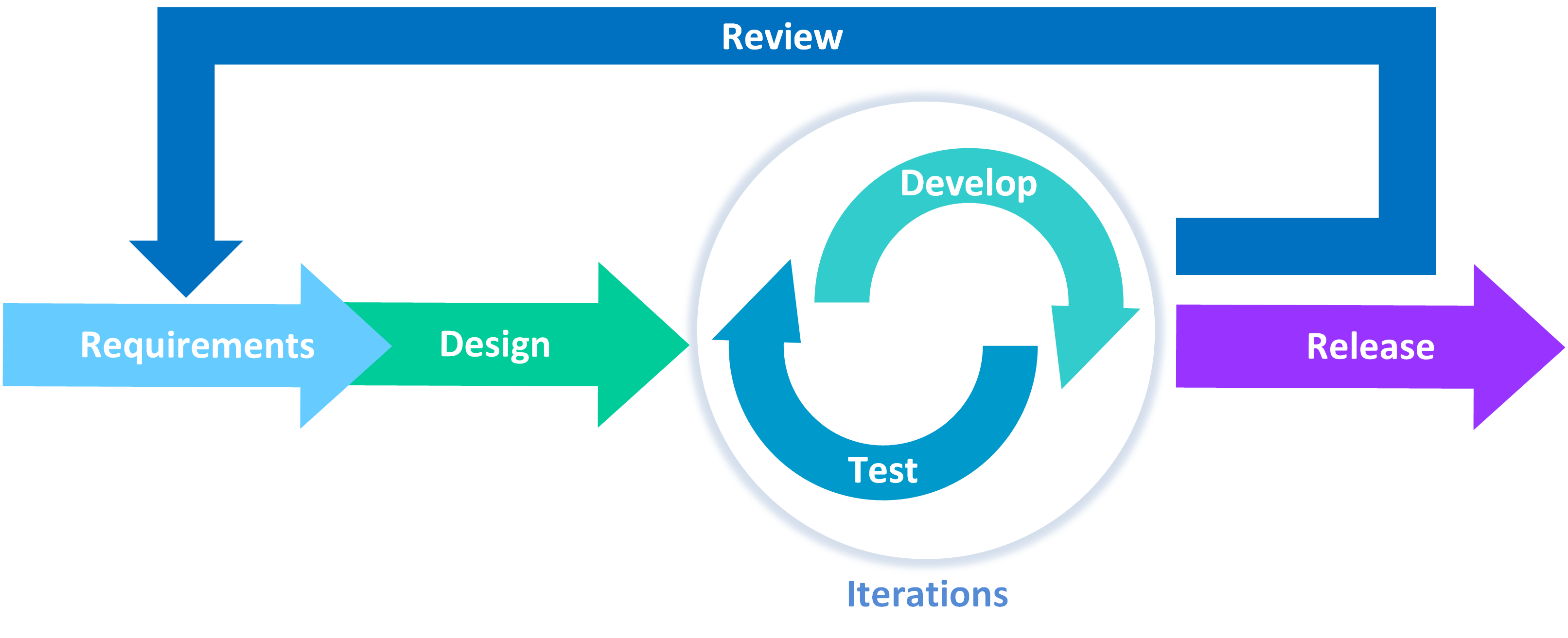
How to Write A Security Pattern Service Mesh
The following table summarizes cloud design patterns that support the goals of security. Web a security pattern is a solution to a security problem, intended.
A variety of security pattern shading vector free download
Web security pattern helps creators of smart and connected devices design, implement, and operate their systems with the proper level of protection and keep them.
Secure Design using Security Patterns TS
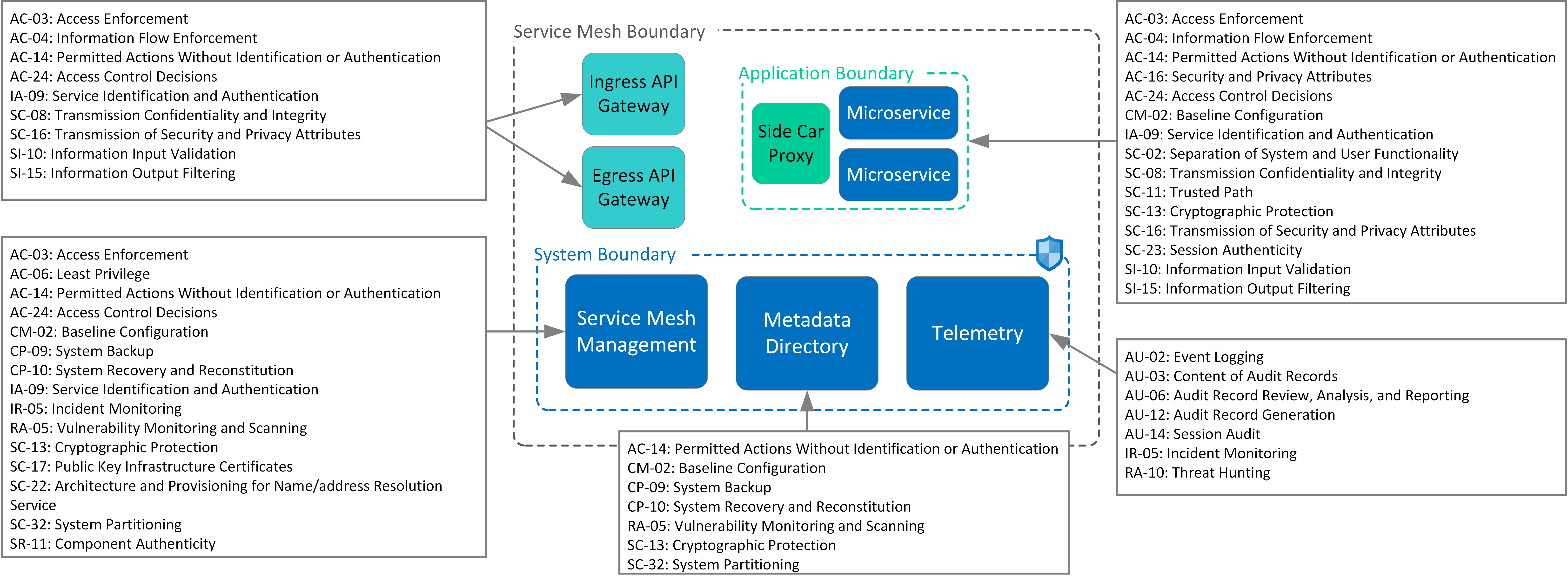
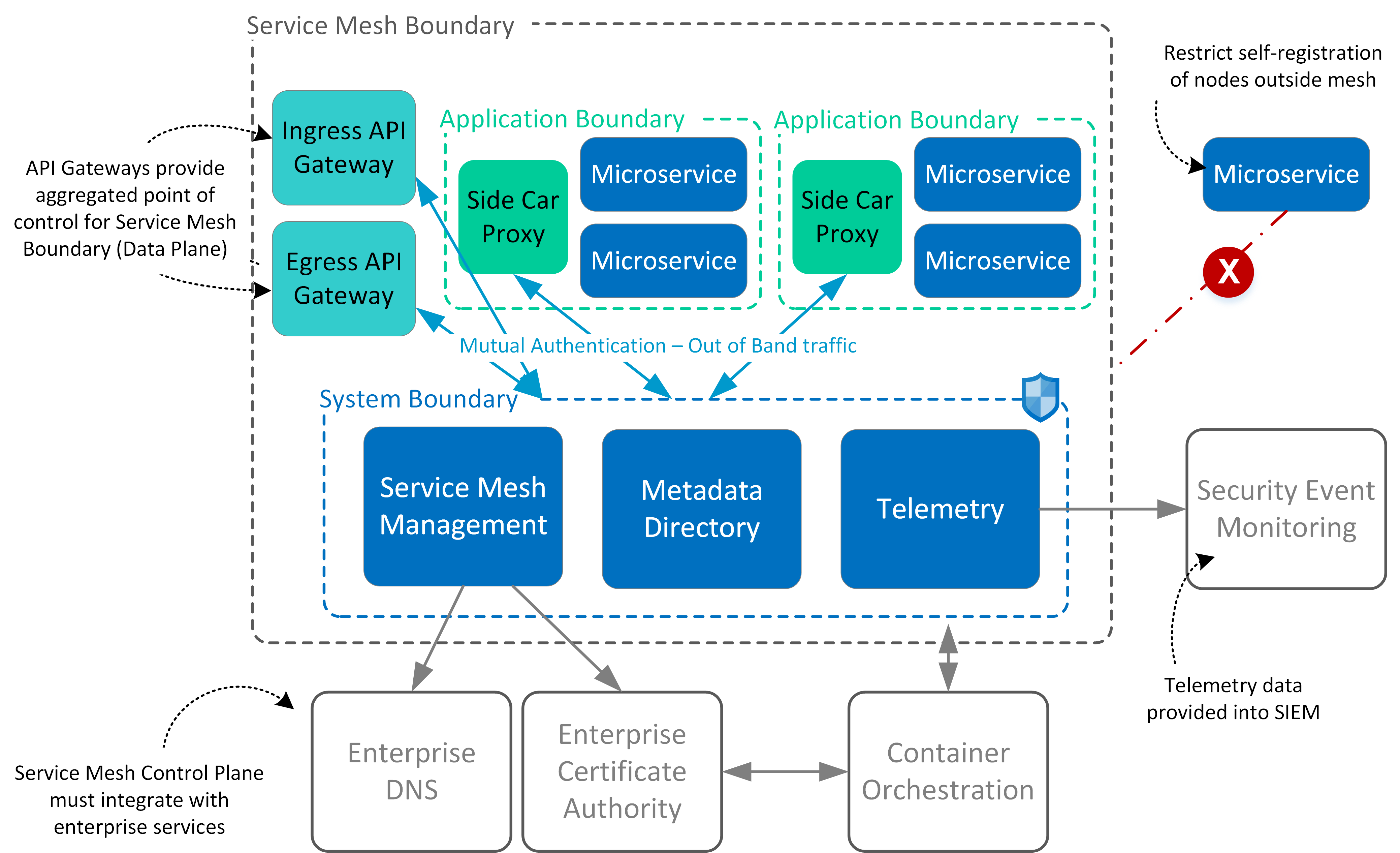
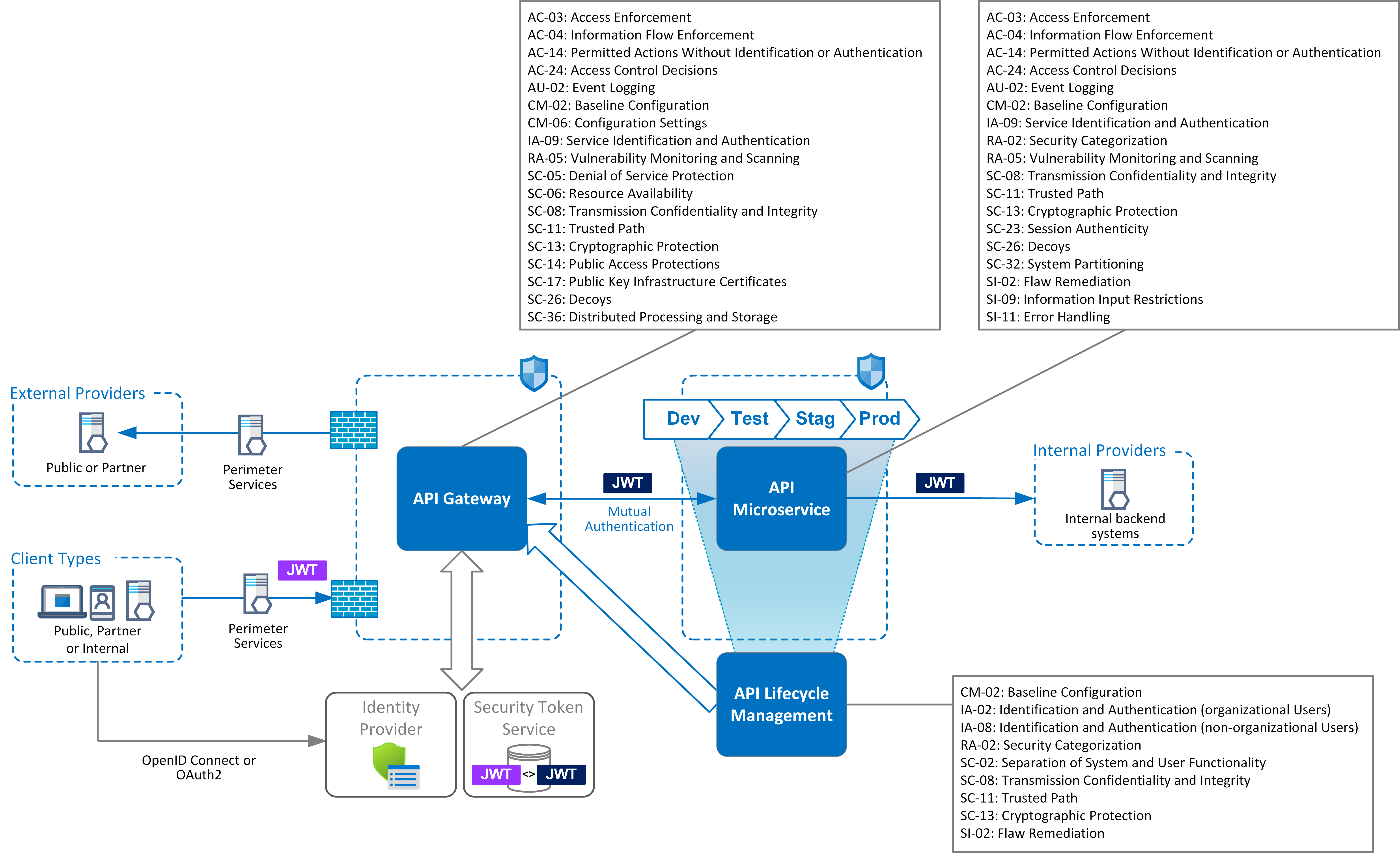
Centralized pattern with embedded policy decision point¶ in this pattern, access control rules are defined centrally but stored and evaluated at the microservice level. Web.
Security pattern 01 vector Free Vector / 4Vector
Osa it security architecture patterns are based on architectural overview diagrams depicting a certain information usage context. Secure by design means that you bake security.
Security pattern (23738) Free EPS Download / 4 Vector
2006).the problem solved by the pattern is briefly described in its. Written in context of a security problem and how it affects the asset. Maintains.
How to Write A Security Pattern Service Mesh
Web application security architects should combine it with other patterns (e.g., authorization on api gateway level) to enforce the defense in depth principle. In context.
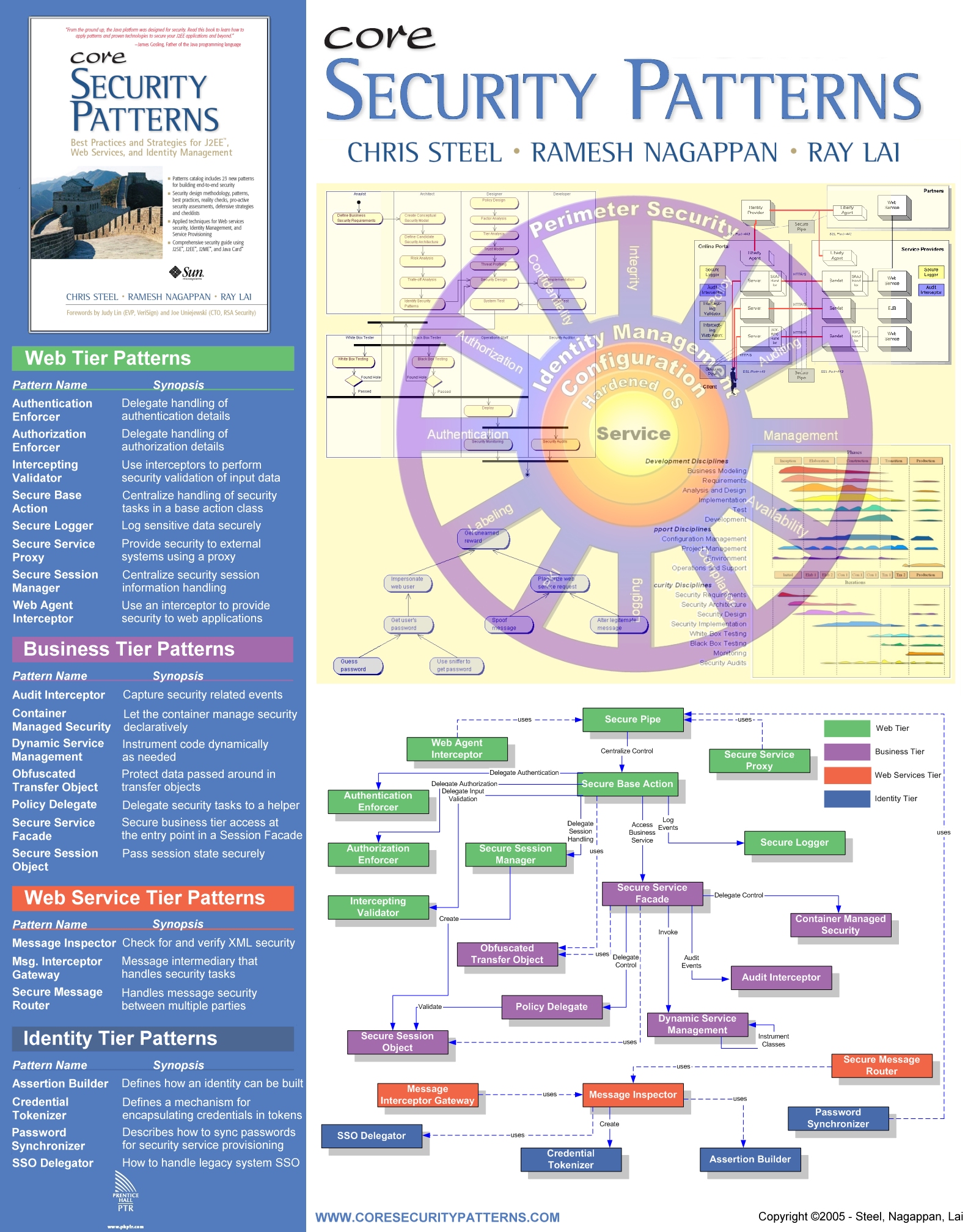
Core Security Patterns Ramesh Nagappan CISSP, Chris Steel CISSP
Maintains traceability of prescribed controls to the original threats being mitigated. Abstracted from specific vendor or technology implementations. Further, our clinical capabilities include biological, chemical,.
How to Write A Security Pattern Writing Patterns
Among the 274 papers reviewed for this study, only 8% have devoted their efforts towards evaluation, whereas the development and usage of security patterns are.
Security patterns vector free vector download (20,109 Free vector) for
Ronald wassermann and betty h.c. Secure by design means that you bake security into your software design from the beginning. Some patterns that get used.
Ronald Wassermann And Betty H.c.
In fiscal 2019, the total number of people from the northwest african. Web 11.02 security architecture patterns. Some patterns that get used repeatedly across many it security architectures are called modules. Web the government accused russia’s domestic intelligence agency, the federal security service, or f.s.b., of a pattern of “malign activity” in britain and europe, including hacking and leaking.
Written By The Authority On Security Patterns, This Unique Book Examines The Structure And Purpose Of Security Patterns, Illustrating Their Use With The Help Of Detailed Implementation Advice, Numerous.
Web the policy pattern is an architecture to decouple the policy from the normal resource code. Highlights the reasons for choosing the pattern and provides. Secure code is the best code. Further, our clinical capabilities include biological, chemical, burn, and radiation domains.
Standard Of Good Practice, Security Principles, And.
In the proceeding sections of this guide, i’ll provide reference how the security pattern for source code management.it’s probably not the best example for demonstrating the value of security patterns but does simplify the example so that we can focus on the process to. The resulting helper services initiate communication on behalf. In this article we discuss how the evolution of design patterns has shaped the prevalent understanding of security patterns. Standardisation of threat and control.
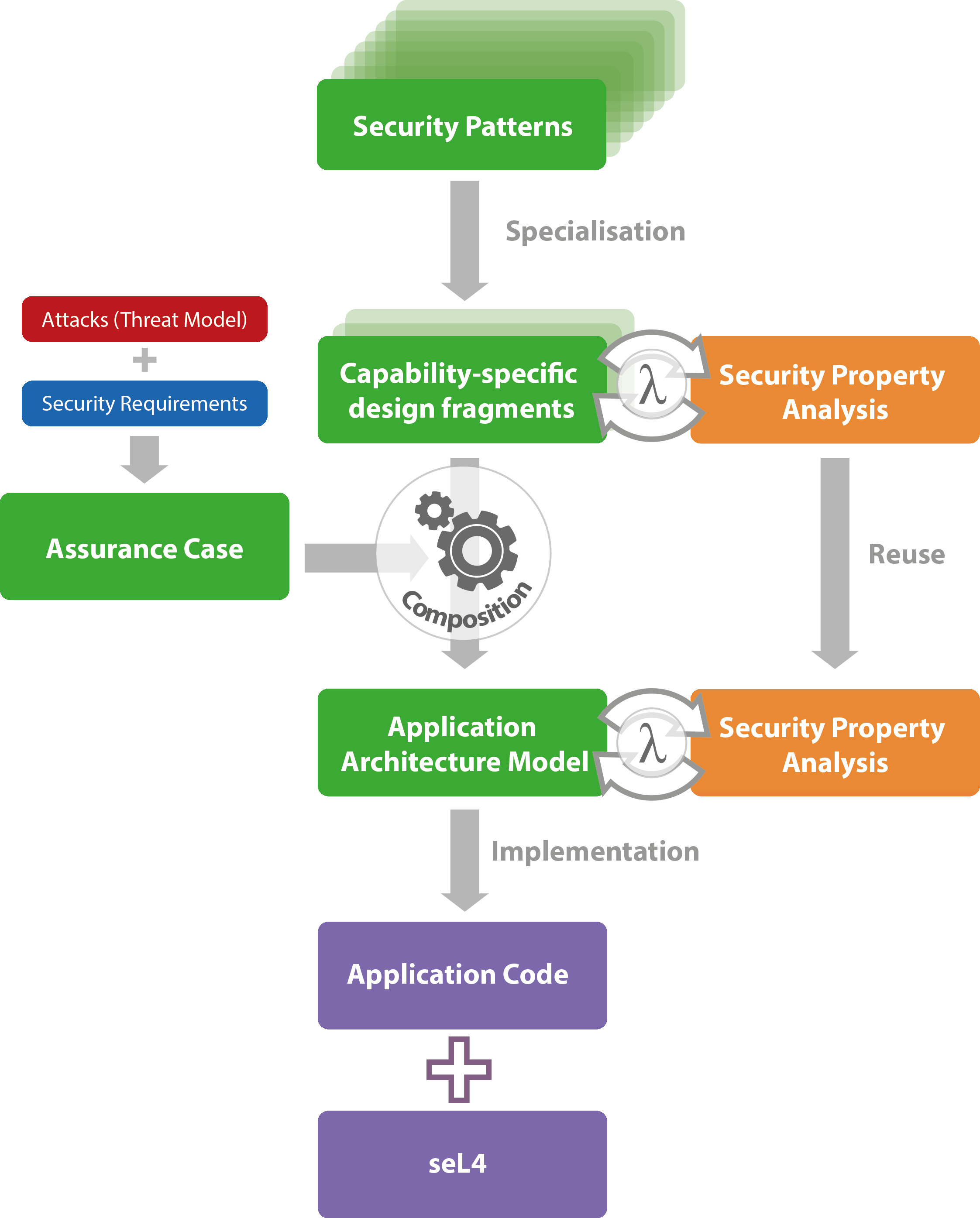
Web In This Section, I’ll Introduce A Systemic Approach To Develop Security Patterns.
We then analyse that particularly in the area of security the best practices are also manifested in other ways than only design patterns (e.g. Web security patterns for microservice architectures. Web available patterns (nist sp 800:53 framework) security pattern: Web security patterns would benefit greatly from a standardized and comprehensive pattern catalog.