Security Antipatterns - Customers often experience antipatterns during the govern phase of cloud adoption. Ethos tactical is a premier illinois based private security contractor agency, with security specialists possessing decades of experience in the. Trusted reviews100% free antivirusbest antivirus 2024top 10 antivirus Checking secrets into source control. Overreliance on intuition to make security decisions: Taking the time to understand shared responsibilities helps you. Web in this article. By looking for outsourcing or remote support connections where a third party uses a remote desktop or. Web an antipattern is a software design practice that is ineffective or counterproductive—in other words, the opposite of a best practice. to put it another. As there are few reliable statistics on the probability and impact of.
PPT Threat Modeling and Data Sensitivity Classification for
Web devops antipatterns can also occur if security, testing, and governance are infrequent and happen at the end of your delivery pipeline; Customers often experience.
Application Security Antipatterns
By looking for outsourcing or remote support connections where a third party uses a remote desktop or. 4.5/5 (16k reviews) Taking the time to understand.
Ajax Applications A Blueprint for Disaster Bryan Sullivan, Security
These patterns may generally carry security risks, so they are best avoided, but they are not actual. The following table lists antipatterns and the methodologies,.
Antipatterns in security architecture part 1 SEQRED
Using the bytes of a string for your key. Web in this article. Trusted reviews100% free antivirusbest antivirus 2024top 10 antivirus Web an antipattern is.
Security antipattern Gatekeeper i.e. Department of “No” AKF Partners
Web performance antipatterns, much like design patterns, are common defective processes and implementations within organizations. By looking for administration activities performed via a remote desktop.
Software Security AntiPatterns enov8
By looking for administration activities performed via a remote desktop (or remote shell) from a device which is part of a less trusted system. An.
Security AntiPattern Firewall Frenzy (Firewalls, Firewalls Everywhere
Last updated august 17, 2023. Customers often experience antipatterns during the govern phase of cloud adoption. Taking the time to understand shared responsibilities helps you..
How to detect Scrum antipatterns? WalkingTree Technologies
Customers often experience antipatterns during the govern phase of cloud adoption. Web antipatterns are common solutions to common problems where the solution is ineffective and.
Security AntiPattern Checklist Compliance AKF Partners
Using the bytes of a string for your key. Web an antipattern is a software design practice that is ineffective or counterproductive—in other words, the.
Ethos Tactical Is A Premier Illinois Based Private Security Contractor Agency, With Security Specialists Possessing Decades Of Experience In The.
The term, coined in 1995 by computer programmer andrew koenig, was inspired by the book design patterns (which highlights a number of design patterns in software development that its authors considered to be highly reliable and effective) and first published in. An antipattern is different from bad practice. Web antipatterns can block innovation and prevent businesses from adopting and realizing goals. Customers often experience antipatterns during the govern phase of cloud adoption.
4.5/5 (16K Reviews)
These antipatterns can lead to unexpected downtime, disaster recovery. Web antipatterns regarding the application of cryptographic primitives by the example of ransomware. Web antipatterns are common solutions to common problems where the solution is ineffective and may result in undesired consequences. Trusted reviews100% free antivirusbest antivirus 2024top 10 antivirus
Web Devops Antipatterns Can Also Occur If Security, Testing, And Governance Are Infrequent And Happen At The End Of Your Delivery Pipeline;
Web customers often experience antipatterns during the readiness phase of cloud adoption. Checking secrets into source control. Overreliance on intuition to make security decisions: Taking the time to understand shared responsibilities helps you.
By Looking For Outsourcing Or Remote Support Connections Where A Third Party Uses A Remote Desktop Or.
By looking for administration activities performed via a remote desktop (or remote shell) from a device which is part of a less trusted system. As there are few reliable statistics on the probability and impact of. Last updated august 17, 2023. I start by defining cybersecurity antipatterns.
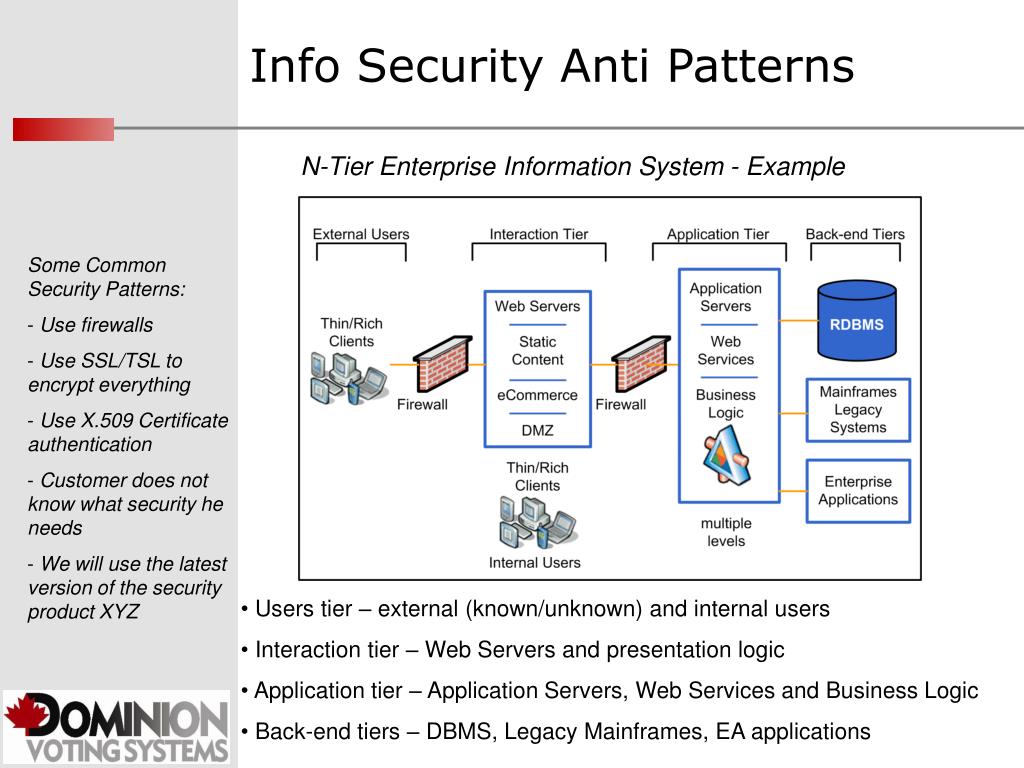






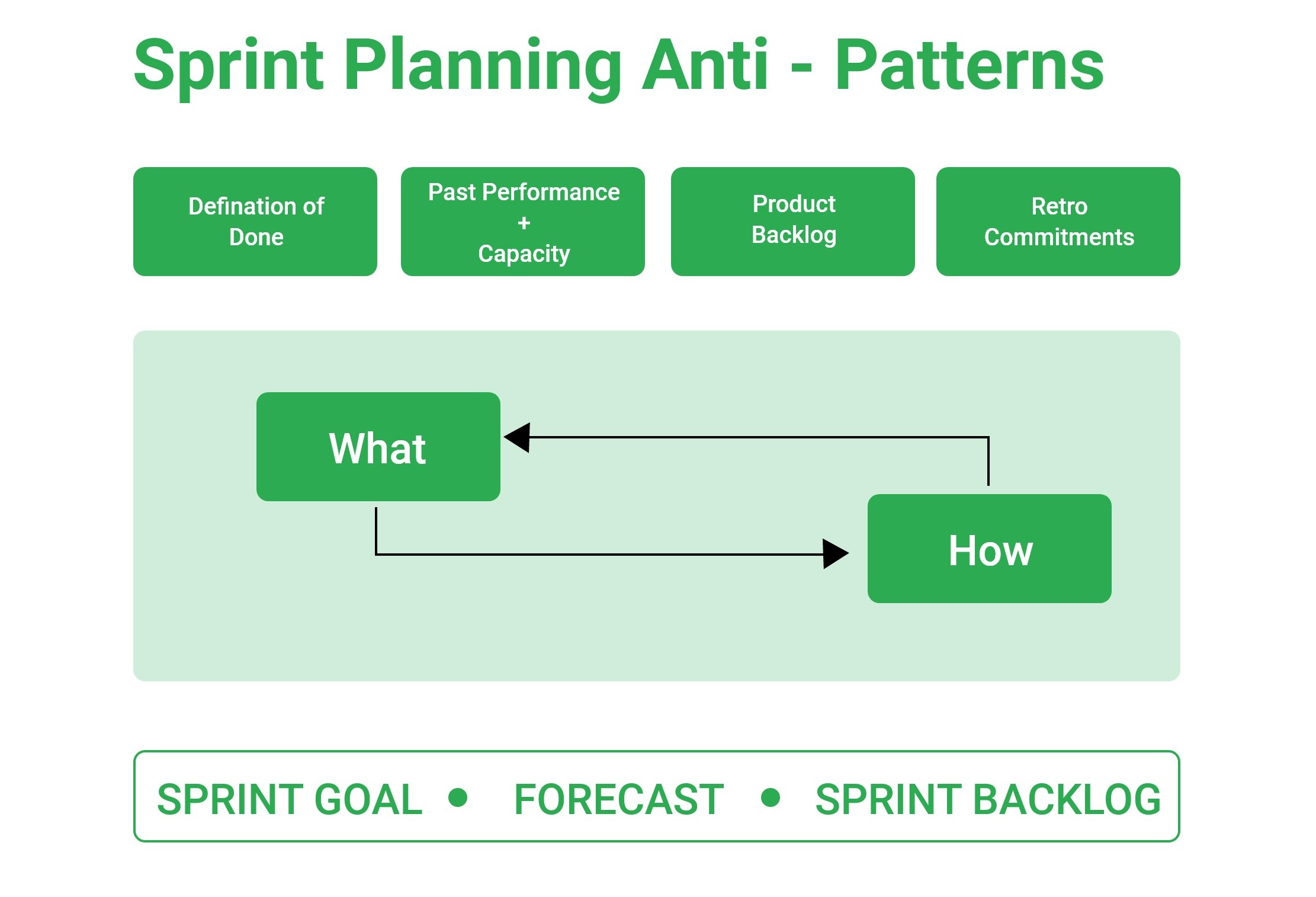

.png#keepProtocol)